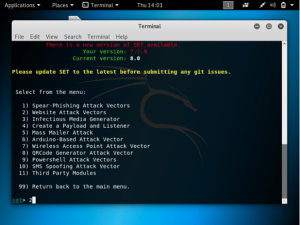
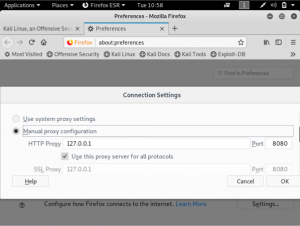
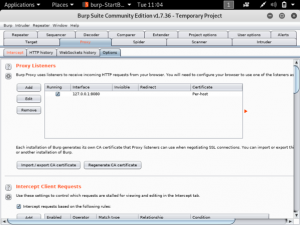
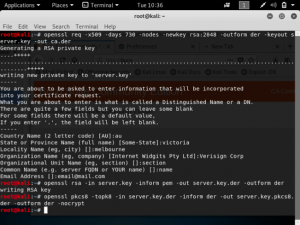
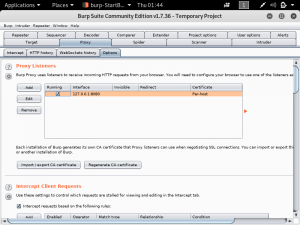
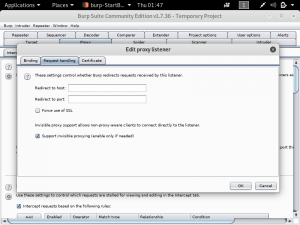
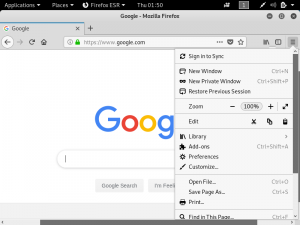
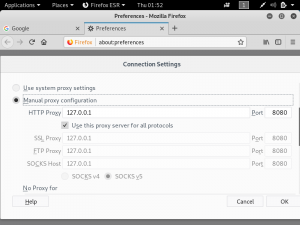
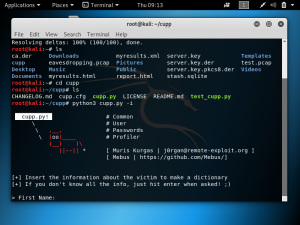
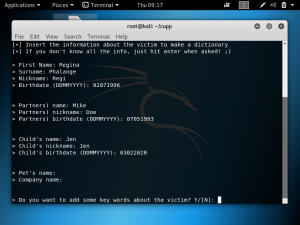
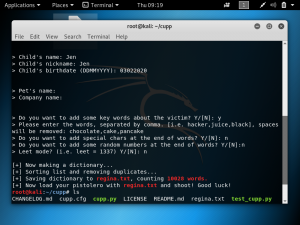
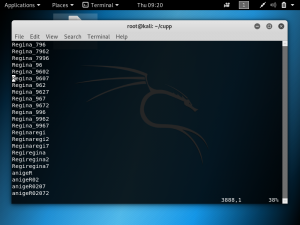
Cloudflare provides the services of a Content Delivery Network and at the same time enhances the security of websites. Cloudflare is easily setup for websites regardless of the platform. What Cloudflare does is it stops malicious traffic from reaching the website’s server. Any traffic requesting to access the website gets routed through Cloudflare’s network. It has its own domain name server services, so any website that uses Cloudflare will not have their real IP public.
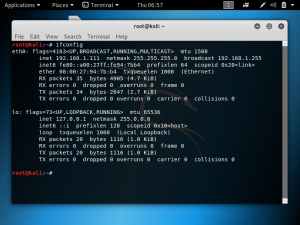
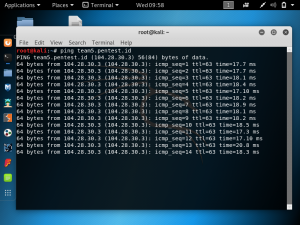
As shown below, running the command ping team5.pentest.id gives the IP address 104.28.30.3.
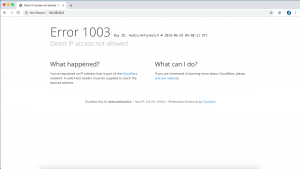
However, if we try to access the website through that IP address, we get the following Cloudflare error.
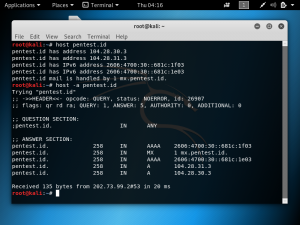
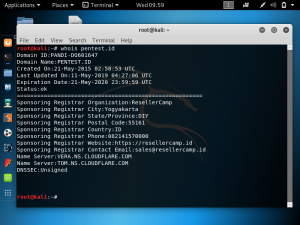
If we check the domain pentest.id using the command whois pentest.id, it shows that the name server is Cloudflare. This verifies that 104.28.30.3 is the Cloudflare IP and not the real IP.
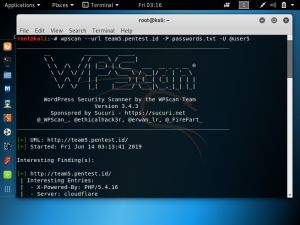
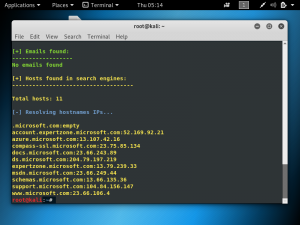
There are various methods to find the real IP of a website behind Cloudflare. The simplest one and probably the first one that should be tried is Censys.io. To use censys.io, all you need to do is input the domain that you are targeting. As shown below, censys.io gives us an IP address along with the OS, open ports, etc.
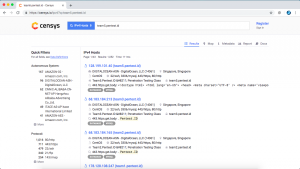
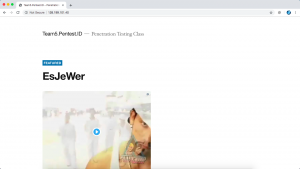
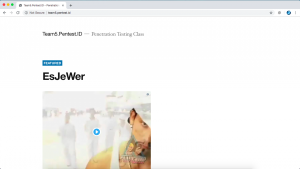
The IP address detected by censys.io is 128.199.101.40. We need to make sure that this is the correct IP of the domain. One thing you can do is try to access the website through the IP address as shown below. We see that the IP address detected by censys.io leads to team5.pentest.id.