Before performing a penetration test, it is important to set up a virtual machine to be more secure. Two things to download are Oracle VM VirtualBox and Kali Linux. VirtualBox is a software that imitates the virtual components of a computer. Kali Linux is a Linux operating system that was developed for the purpose of penetration testing. It is highly convenient as it has over 300 penetration testing applications. Kali Linux can be downloaded here https://www.kali.org/downloads/.
The first thing to do is install VirtualBox. Once VirtualBox is installed, open the application and a screen as shown below will be shown:
Kali Linux will be installed within VirtualBox. To add a new virtual machine, click on the “new” button and you will see the screen as shown below:
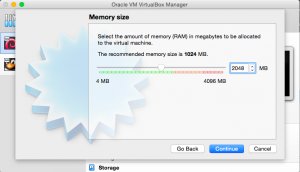
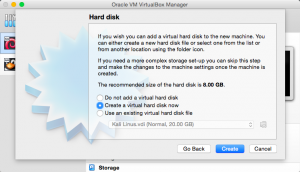
Give the virtual machine a name, for example, “Kali Linux”. Set the type to “Linux” and the version to Debian (64-bit). Click “continue”. The next part is setting the amount of RAM that will be allocated to the virtual machine. Half of your computer’s total RAM is sufficient. After clicking “continue”, select the option “Create a virtual hard disc now”. Click “create”.
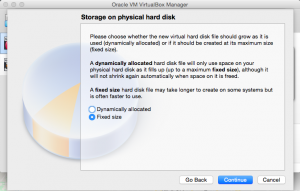
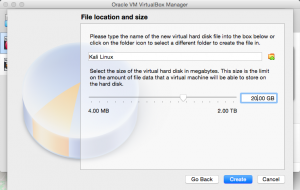
The next part is to choose between dynamically allocated storage or fixed storage. Once this is done, set the amount of storage to be allocated. This depends on how much free storage is available in your computer. Click “create”.
In the main page, the virtual machine you just created will be among the list of machines.
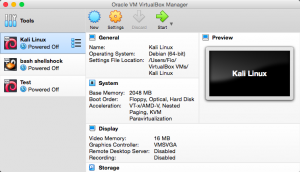
Select the virtual machine and click the “start” button and you will see the screen as shown below. There is still no virtual optical disk file selected, so search for the Kali Linux disk that you have downloaded in the beginning.
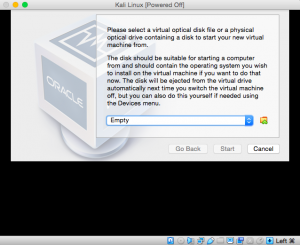
Once the disk is selected, your virtual machine will start and there will be options to set up Kali Linux. When you see the screen as shown below, select “graphical install”.
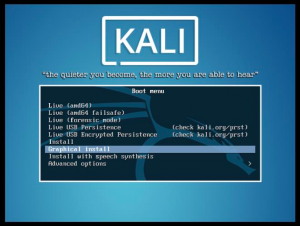
Following this will be selecting language, location, locales, keyboard, timezone, etc. Kali already has a Root User named “root” and the password is “toor”. It is recommended that you change this password.
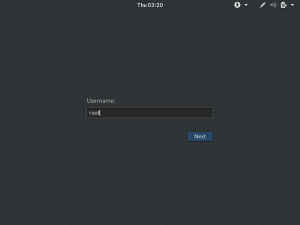
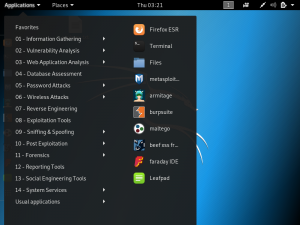
Once you are logged in, you will see the screen as shown below:
As you navigate to the “application” dropdown, you will see the available tools.