Before we can proceed to brute force passwords for a particular user, we need to have a list of passwords. CUPP or Common User Passwords Profiler works by asking for basic information about the target such as their first name, last name, birthday, spouse, children, pets, occupation, etc. It then uses that information to generate a list of possible passwords.
To start using CUPP, we first need to clone the repository from github. In the command line, type: git clone https://github.com/Mebus/cupp.git.
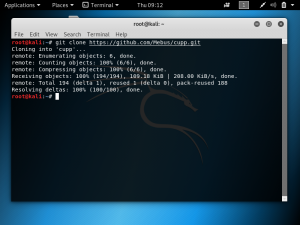
Once its cloned, cd to the directory. You can list out the folders and files in the current directory by typing “ls”. As shown below, there is the folder “cupp”, so we type: cd cupp.
To run the tool, type: python3 cupp.py -i.
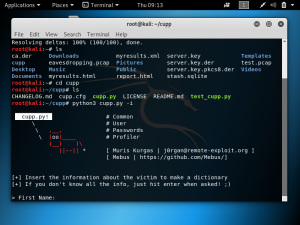
CUPP will then ask you to input information about the target. As seen in the screenshot below, it will ask for first name, surname, nickname, birthdate, partner, children, pets, and company. If you are unsure you can press “enter” to skip. It is optional to add a few keywords related to the target.
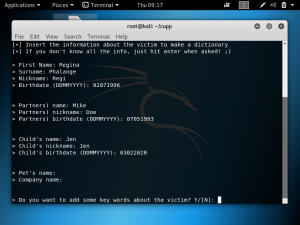
Once you have included such information, CUPP will generate a password dictionary.
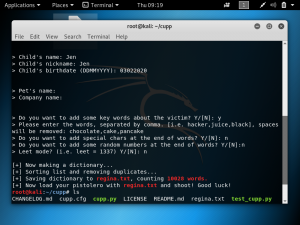
The screenshot below shows the password dictionary generated by CUPP.
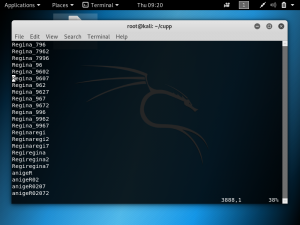
Now that we are aware of such a tool, it is important to always think of a strong password. Try to not use common passwords that include your name or birthday, as they are easy to guess and not secure against a brute force attack.