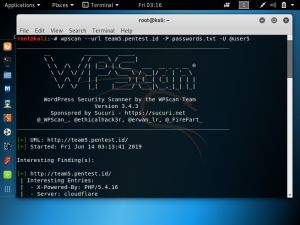
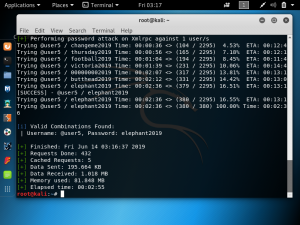
When you are intercepting network traffic with BurpSuite, you may get an SSL error saying that your connection is not secure. Websites may not load properly and the padlock symbol next to the URL will have a warning lock. In order to prevent this, you can create a custom certificate.
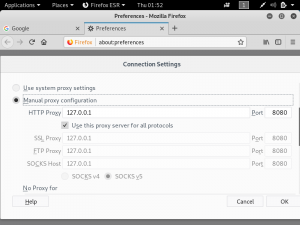
In Kali Linux, open the browser, navigate to “preferences” and find “network proxy”. Click on the settings and set it to “manual proxy”.
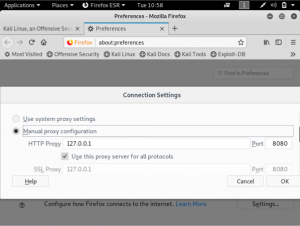
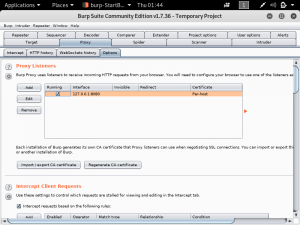
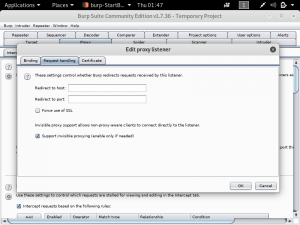
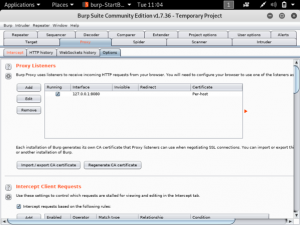
In BurpSuite, navigate to “proxy”, then “options”. You will see that the proxy listeners is the one set previously in the browser.
To create the certificate, we will be using 3 commands in terminal as shown below:
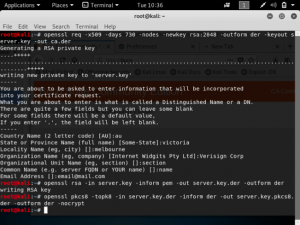
The first command is: openssl req -x509 -days 730 -nodes -newkey rsa:2048 -outform der -keyout server.key -out ca.der
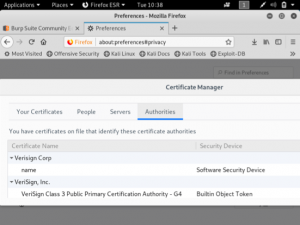
After this command, OpenSSL will ask you to enter some details for the certificate. This includes a 2-letter country code, state or province, city, organisation, unit name, common name and an email address. The example above sets the organisation name to Verisign Corp.
The second command is: openssl rsa -in server.key -inform pem -out server.key.der -outform der
The third command is: openssl pkcs8 -topk8 -in server.key.der -inform der -out server.key.pkcs8.der -outform der -nocrypt
Now when you go to “files”, you will see that three files have been created.
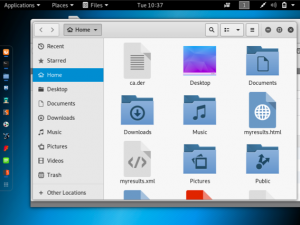
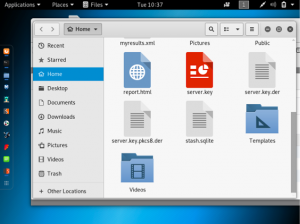
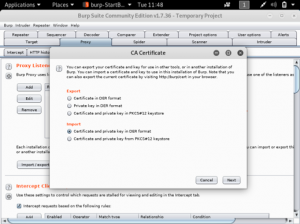
Return to the BurpSuite window and select “import/export CA certificate”. Then, select “certificate and private key in DER format”. The certificate file is ca.der and the private key file is server.key.pkcs8.der.
Return to the browser, open “preferences” and click on the padlock.
Scroll to the bottom of the page and click on “view certificates”.
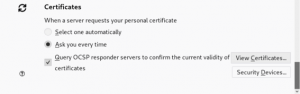
Next you will import the ca.der file to the browser. Select “Trust this CA to identify websites”.
Verisign Corp is now included in the certificates:
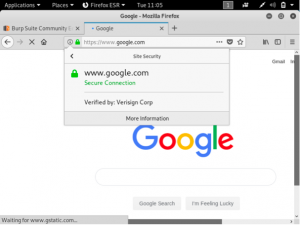
The websites that you open in the browser now has an SSL certification from Verisign Corp.
Reference: https://portswigger.net/burp/documentation/desktop/tools/proxy/options