Social engineering is the act of exploiting human vulnerabilities to obtain sensitive information. It relies on trust, because with a trusting relationship, the target will be more likely to share information.
Methods of social engineering include: impersonation, reciprocation, influential authority, scarcity, and social relationship.
SET is a Social Engineering Toolkit. We will be using this tool to clone a popular website, applying the method of impersonation.
To start with SET, in Kali Linux navigate to “applications” > “social engineering tools” > “social engineering toolkit”
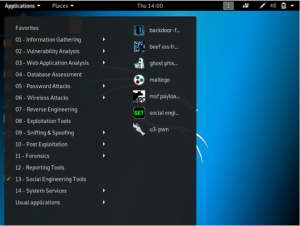
Once SET has started, it will give you a number of options.
First, choose 1: social engineering attacks
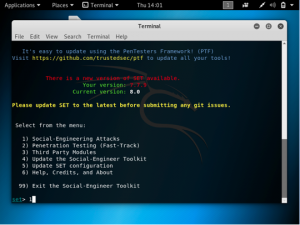
Choose 2: website attack vectors
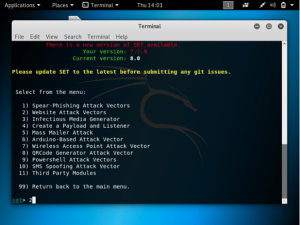
Choose 3: credential harvester attack method
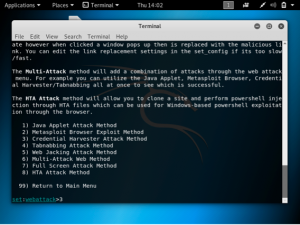
Choose 2: site cloner
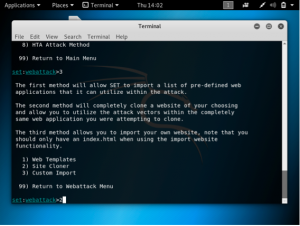
Next, input the IP address of the attacking VM. This can be found through the ifconfig command. Include also the URL of the website you are cloning. In this example, https://www.twitter.com.
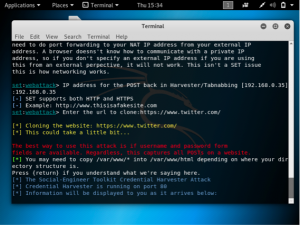
If you go to the browser and type in the IP of the attacking VM, a clone of twitter.com will be displayed. If you input a username and a password into the login box, the information will be displayed in your Kali Linux command line.
This is an example of the impersonation method, because we are impersonating the login page of a well known website. The victims who visit this cloned website will assume it is the real one and would input their username and password. They will not be aware that their username and password have been sent to the attacker.