Nikto is a vulnerability scanner that operates via command line to scan websites for outdated server, dangerous files, directories, etc. It performs a large number of tests against a website to gather and report back security vulnerabilities that can be exploited. As it is able to find hard to detect problems, it is a popular tool among system admin and security professionals.
To scan a target website, use the command: nikto -host <target>. In the target space, it can either be a domain or an IP address.
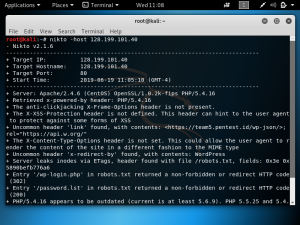
In the example below, we are doing a Nikto scan of a website with the IP address 128.199.101.40. So the command is: nikto -host 128.199.101.40
In this example, the IP address is used because using the domain would lead to a scan of the Cloudflare SSL IP address. As shown below, we are able to find information regarding the server which is Apache/2.4.6 and the OS is CentOS. The scan also detected a robots.txt file that has directories such as /password.lst. It was also found that the PHP version is outdated.
The weakness of Nikto is the fact that it is not stealthy. Nikto makes over 2000 HTTP GET requests to the web server, which means that a Nikto scan should be detectable. The number of GET requests can be used to test the system’s Intrusion Detection System (IDS).