Devices such as laptops, smartphones, tablets, etc. create network traffic when they are connected to the same network. When an attacker performs packet sniffing of the network traffic, they are able to view the activity on those devices such as visited websites. TCPDump is a command-line packet analyser that allows users to intercept and view packets that are being transmitted over a network.
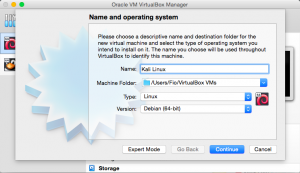
To test these tools, prepare 2 virtual machines. One will be the attacker and the other will be the victim. If Kali Linux is already installed, you can simply clone it. For both machines, click “settings” and “network”. Here, set the network to “bridged adaptor”.
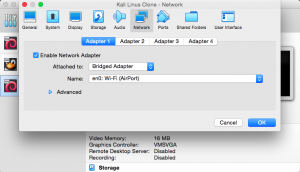
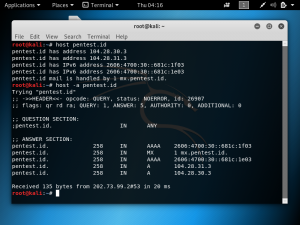
Run both machines and type the command “ifconfig” in terminal to get the IP addresses. As shown in the screenshots below, the attacker’s IP address is 192.168.1.111 and the victim’s IP address is 192.168.1.112.
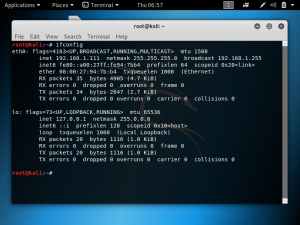
In the attacker’s command line, type: tcpdump -vvn -i eth0 host 192.168.1.112 -w test.pcap. After pressing enter, try to browse various websites in the victim’s browser. As the victim browses, the attacker’s machine will eavesdrop on all the packets transmitted and received by the victim.
![]()